What is Proxy Server And Different Types of Proxies 5,329 Views
A proxy server is a computer or usually set of computers that act as an intermediary between a client computer and a web server. It enables client computers to make indirect requests through it for resources or services such as web pages, videos, PDF files, etc.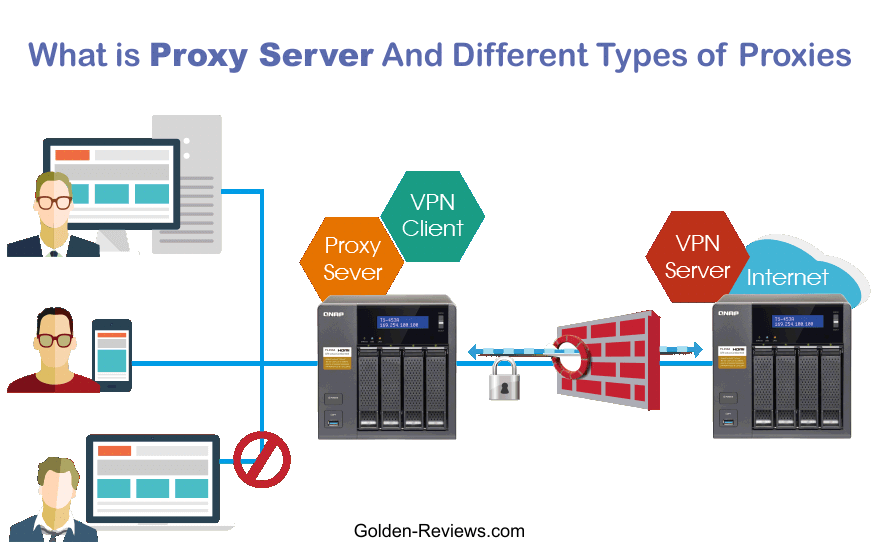
Here’s how it works : A client contacts the proxy server, requests a file, web page or other resource from a different server. If the proxy server has the requested file or web page in its cache, the proxy server returns the file or web page to the client. Otherwise, it connects to the requested server, provides the client with the file or webpage, and then save it in its cache for later use. Because of their position between client and the requested resource, proxy servers can potentially alter a client’s request or the server’s response.
The IP address of the client computer (your computer) stays hidden to the web server. Only the proxy has information on the IP address of the client computer (individual computer user). To protect customers’ privacy, companies that provide the proxy services claim that they delete the logs frequently. In practice, not all web proxies are created equal. There is a huge variance in how a web proxy can be set up and its technical capabilities. Decoding how a web proxy provides clients with enhanced privacy and security primarily depends upon how the individual proxy handles the individual data packets (the information postcards of the Internet) traveling between two computers, use of encryption techniques, and the intent of the proxy owner.
The web proxy takes the message from Alice, and adds its own IP address to the network section of each data packet from Alice. This additional information functions like a postcard that has had a new return address stuck on top of the old. Bob gets a message sent from the new IP address, his response goes to the proxy, and then sends the message on to Alice. A shielded IP address from a web proxy may be sufficient for computer users to get around some site restrictions on content. For example, someone in Europe visiting a US site that limits access to computer users with an American IP address can access the site with a shielded IP address from the web proxy. However, site access is different from security. If proxy communication with the site is not encrypted with HTTPS protocol, data packets can still be easily dissected to uncover the original user’s IP address.
Alice had me to ask you “What time is it?”
Some web proxies will not cover up Alice’s address. Similar to a “Forward to” note on a letter, they can add their IP address to data packet headers as HTTP_FORWARDED or HTTP_VIA without covering up the original IP address. For those wanting to shield their IP address and their identity, this is an incomplete solution. As the name suggests, for most proxy servers, the IP address is only shielded for web browser activities – not for other connected online apps. Skype VOIP, as just one example, collects and can broadcast a user’s real IP address.
I’ll pass on most of the messages - but I might read it or take notes.
• By definition, web proxies are well placed to filter and restrict content. They are also positioned to read unencrypted messages and to keep logs of who is sending messages to where. With the unencrypted HTTP protocol, data packets are open postcards that can be easily sniffed out and read - even if the users’ IP address has been shielded.
• Web proxies also provide limited security to users because they are not technically structured to warn users if data packets have been altered during transit or to certify that only Alice and Bob are in a secure, point-to-point conversation. While some web proxies may include encryption, it is not a guaranteed element.
• For consumers wanting to surf the Web privately and securely, a better solution is a VPN (virtual private network). A VPN encrypts all your internet communications while hiding your IP address to protect your privacy. What this means is that anyone trying to sniff your traffic will not be able to decipher it since it’s encrypted.
• Transparent Proxy : This type of proxy identifies itself as a proxy server and makes the client’s original IP address visible through the HTTP headers. They are transparent in that the user’s IP address is exposed and that the client user might not know that he or she is using the proxy. Transparent proxies may enable users to get around simple IP bans but because they do not hide or encrypt the user’s IP address, do not provide any anonymity.
• Anonymous Proxy : This type of proxy server does not make the client’s IP address available to the contacted site although it still identifies itself as a proxy server. While detectable, this gives a moderate level of anonymity for most users. Distorting Proxy - This type of proxy server identifies itself as a proxy server, but make an incorrect original IP address available through the HTTP headers on the data packets.
• High Anonymity Proxy : This type of proxy server presents itself as an independent device as it does not identify itself as a proxy server or make the client user’s original IP address readily available. Its level of anonymity against deep packet analysis varies on the use of HTTPS protocol.

Here’s how it works : A client contacts the proxy server, requests a file, web page or other resource from a different server. If the proxy server has the requested file or web page in its cache, the proxy server returns the file or web page to the client. Otherwise, it connects to the requested server, provides the client with the file or webpage, and then save it in its cache for later use. Because of their position between client and the requested resource, proxy servers can potentially alter a client’s request or the server’s response.
Using Web Proxy Server to Cache Files or Web Pages
Caching Web proxies can speed up access to frequently accessed web pages, by building a cache of frequently requested web pages or files. By speeding up the network traffic, it also provides needed reliefs to server load. After getting a client’s request for a website URL or file, the proxy first looks in its own cache. If the data is in the cache, this immediately goes to the requesting client. Otherwise, the proxy asks for the connection to the server, and forwards the results to the client after keeping a copy for itself. The proxy keeps its cache updated by discarding the least used or oldest files.Using Web Proxy Servers to Restrict or Unblock Internet Traffic
Companies frequently use web proxy servers to restrict internet traffic to a single entrance or exit point within the company network. This has dual benefits for the company. Not only it's easier to guard against threats and malware coming in from a single point (by scanning the transmitted content), proxy servers also enable organizations to control employees’ internet activities by filtering content and restricting visits to certain websites. For individual computer users, web proxies are often used for precisely the opposite result - circumvent company internet filters and to browse the Web anonymously by hiding their device’s IP addresses. Many services exist to provide consumers with proxies to surf the web anonymously. By accessing a website via a proxy server, the website that the proxy server connects to is only able to track the IP address of the proxy server.The IP address of the client computer (your computer) stays hidden to the web server. Only the proxy has information on the IP address of the client computer (individual computer user). To protect customers’ privacy, companies that provide the proxy services claim that they delete the logs frequently. In practice, not all web proxies are created equal. There is a huge variance in how a web proxy can be set up and its technical capabilities. Decoding how a web proxy provides clients with enhanced privacy and security primarily depends upon how the individual proxy handles the individual data packets (the information postcards of the Internet) traveling between two computers, use of encryption techniques, and the intent of the proxy owner.
Here are three basic communications that a web proxy server might communicate with the users:
What is the current time?The web proxy takes the message from Alice, and adds its own IP address to the network section of each data packet from Alice. This additional information functions like a postcard that has had a new return address stuck on top of the old. Bob gets a message sent from the new IP address, his response goes to the proxy, and then sends the message on to Alice. A shielded IP address from a web proxy may be sufficient for computer users to get around some site restrictions on content. For example, someone in Europe visiting a US site that limits access to computer users with an American IP address can access the site with a shielded IP address from the web proxy. However, site access is different from security. If proxy communication with the site is not encrypted with HTTPS protocol, data packets can still be easily dissected to uncover the original user’s IP address.
Alice had me to ask you “What time is it?”
Some web proxies will not cover up Alice’s address. Similar to a “Forward to” note on a letter, they can add their IP address to data packet headers as HTTP_FORWARDED or HTTP_VIA without covering up the original IP address. For those wanting to shield their IP address and their identity, this is an incomplete solution. As the name suggests, for most proxy servers, the IP address is only shielded for web browser activities – not for other connected online apps. Skype VOIP, as just one example, collects and can broadcast a user’s real IP address.
I’ll pass on most of the messages - but I might read it or take notes.
• By definition, web proxies are well placed to filter and restrict content. They are also positioned to read unencrypted messages and to keep logs of who is sending messages to where. With the unencrypted HTTP protocol, data packets are open postcards that can be easily sniffed out and read - even if the users’ IP address has been shielded.
• Web proxies also provide limited security to users because they are not technically structured to warn users if data packets have been altered during transit or to certify that only Alice and Bob are in a secure, point-to-point conversation. While some web proxies may include encryption, it is not a guaranteed element.
• For consumers wanting to surf the Web privately and securely, a better solution is a VPN (virtual private network). A VPN encrypts all your internet communications while hiding your IP address to protect your privacy. What this means is that anyone trying to sniff your traffic will not be able to decipher it since it’s encrypted.
The Different Types of Proxies
• CGI (Common Gateway Interface) Proxies : CGI proxies are frequently used to circumvent company or school’s restrictions on web use. The user enters the desired URL into the proxy through their browser window. The CGI proxy then displays the requested URL through the browser window. CGI proxies are frequently used to gain access to web sites blocked by corporate or school proxies. They provide limited anonymity as they hide the user’s IP address from the contacted site.• Transparent Proxy : This type of proxy identifies itself as a proxy server and makes the client’s original IP address visible through the HTTP headers. They are transparent in that the user’s IP address is exposed and that the client user might not know that he or she is using the proxy. Transparent proxies may enable users to get around simple IP bans but because they do not hide or encrypt the user’s IP address, do not provide any anonymity.
• Anonymous Proxy : This type of proxy server does not make the client’s IP address available to the contacted site although it still identifies itself as a proxy server. While detectable, this gives a moderate level of anonymity for most users. Distorting Proxy - This type of proxy server identifies itself as a proxy server, but make an incorrect original IP address available through the HTTP headers on the data packets.
• High Anonymity Proxy : This type of proxy server presents itself as an independent device as it does not identify itself as a proxy server or make the client user’s original IP address readily available. Its level of anonymity against deep packet analysis varies on the use of HTTPS protocol.
Published : Mon 05 Mar 2018
Updated : Thu 26 Mar 2020
Updated : Thu 26 Mar 2020


0 Comments